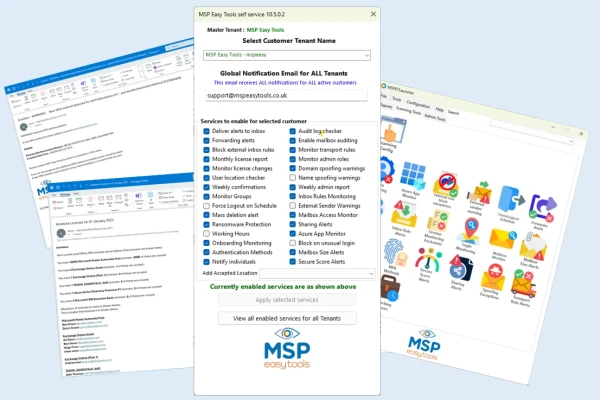
Azure/Entra ID Monitoring & Alerting Tools
|
|
Tool
|
What It Does
|
Why
|
Location Monitoring
|
Alerts you to logins from unfamiliar or unapproved locations. Define trusted IPs, cities, or countries—and even schedule access windows. You can also block access automatically on detection.
|
Most cyber attacks happen from suspicious locations. Monitor exactly what you need, confident that accounts are instantly blocked, if that's what you choose.
|
Admin Role Changes
|
Receive alerts when new admins are added or roles are modified.
|
Admin access is a top target for attackers—stay in the loop.
|
MFA Authentication Methods
|
Get notified when new MFA methods are added. Block potential bypasses through suspicious MFA registrations.
|
Evil proxy attacks make use of authentication methods by registering a bogus method. Unless you are monitoring for this, you'll never know.
|
Azure App Monitor
|
Detect and review new Azure apps. Easily allow trusted ones and flag anything unfamiliar for review.
|
Azure apps are a key way cybercriminals can gain access to systems. Lets you keep on top of this risk
|
Forced Logout On Schedule
|
Automatically log users out from all devices on a schedule—ideal for company shutdowns or security resets. MFA re-authentication is enforced.
|
Could be implemented at business downtimes/ major holiday shutdowns. Removes cyber threat
|
Working Hours Restrictions
|
Disable user accounts during inactive periods to limit risk during off-hours.
|
Security of accounts is massively improved if it can be disabled during inactive periods
|
License Monitoring (with Exclusions)
|
Monitor license allocations and changes across users or departments, with the option to exclude specific users.
|
Allows you to keep on top of license changes and spot if any have been added that shouldn’t have been .
|
Group Changes (External Users)
|
Be alerted when an external user is added to a group—an often-overlooked tactic used by intruders.
|
Cybercriminals will secretly add themselves to a group, so you need to stay in the know.
|
Exchange / Mailbox Monitoring & Alerting Tools
|
External Forwarders
|
Detect and block auto-forwarding rules to external addresses.
|
Quickly spot any forwarders placed on accounts - often used in data exfiltration attacks.
|
Mailbox Delegation Monitor
|
Monitor who has been granted access to key mailboxes. Approve or remove changes quickly.
|
Know rapidly if any permissions are added to key mailboxes and rectify just as quickly.
|
Mailbox Size Alerts
|
Get notified when a mailbox is nearing capacity.
|
Avoid disruption and maintain continuity - no unneeded down-time.
|
Transport & Inbox Rules
|
Be alerted to rules that redirect mail or affect visibility.
|
Identify potentially malicious filters or forwarding settings.
|
External Sender Warning
|
Add a visual alert on emails from outside the organisation. Choose which accounts this applies to.
|
Be clear on any emails that are from external users.
|
Internal Spoofing Protection
|
Detects spoofed emails and flags a warning banner.
|
Make sure that you know if messages are spoofed – at a glance. Keeps your business safer.
|
Inbox Rule Exceptions
|
Allow legitimate rules to run even when inbox rule monitoring is active.
|
Keeping flexibility without compromising safety.
|
Sharepoint / OneDrive Monitoring & Alerting
|
Sharing Alerts
|
Know instantly when files are shared externally
|
Protect your data and reputation
|
Mass Deletion / Change Alerts
|
Receive alerts for large-scale deletions, renames, or moves.
|
Make sure you know rapidly if any SharePoint data is moved, renamed (which could be done with Ransomware attacks) and deleted in large quantities.
|